

Employees reuse passwords, fall for scams, and create backdoors.
Support tickets pile up. Forgotten logins cost time and patience.
Teams, vendors, and contractors still share access—risky and untraceable.
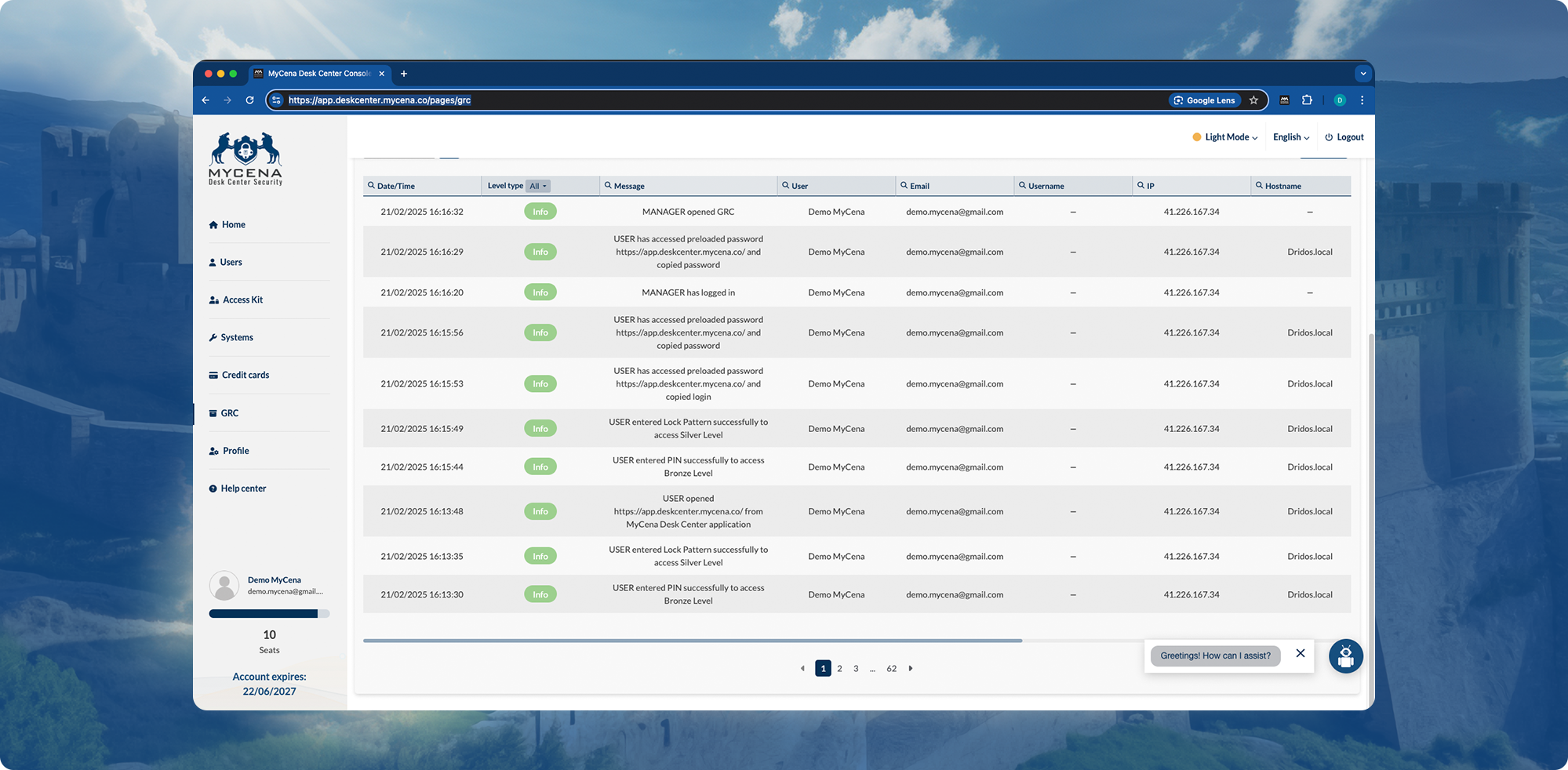
You dread audits. Logs are scattered. Reports are painful.
Ex-employees retain access to systems for weeks. Or longer.
Vendors access systems using passwords you can’t fully control.

– Julia O’Toole, MyCena® Co-CEO
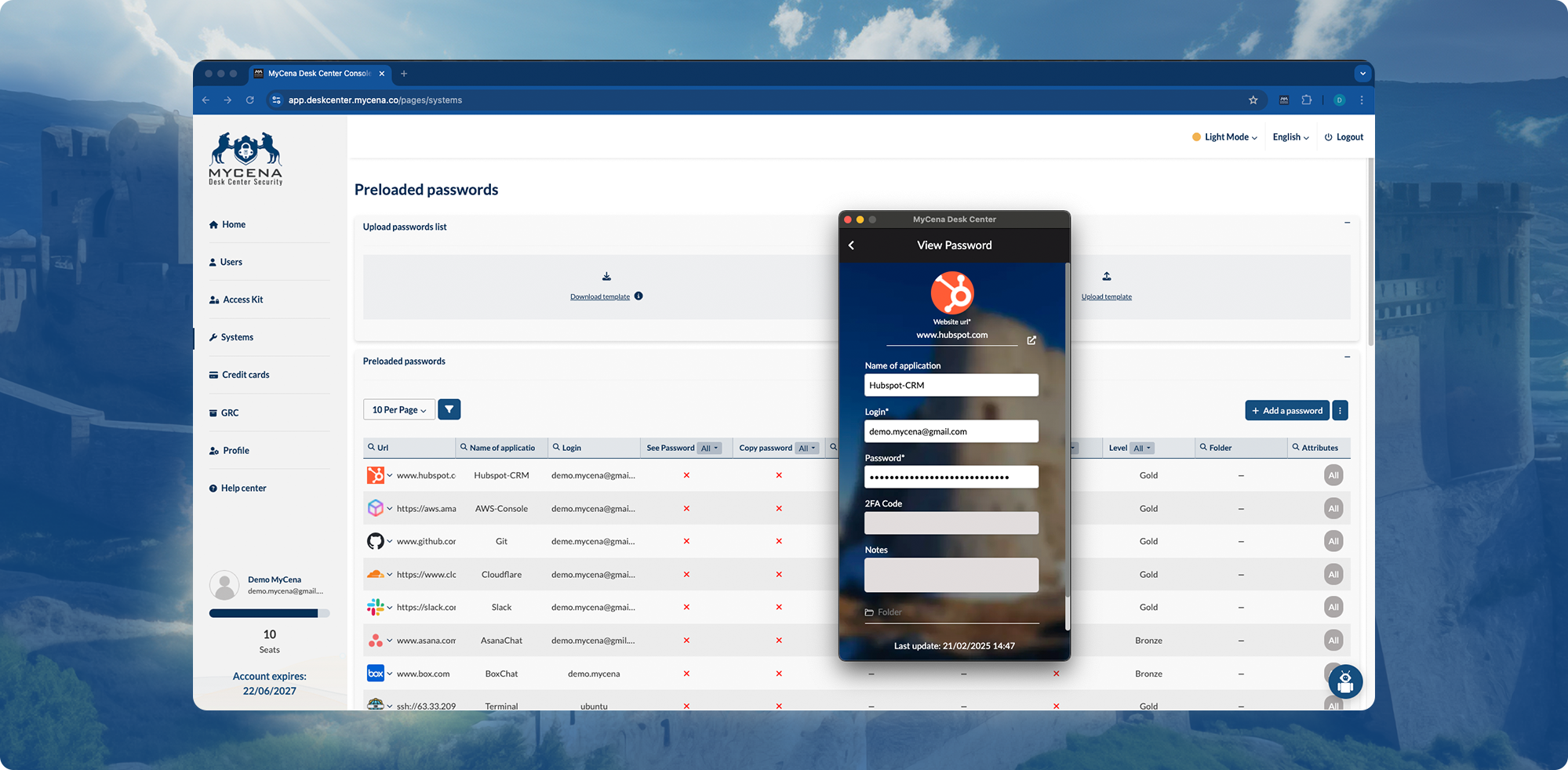
Users never manage credentials—nothing to phish, steal, or leak.
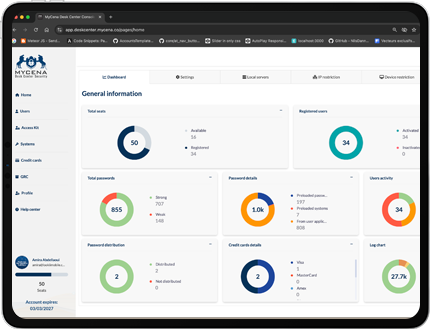
Say goodbye to IT tickets, delays, and forgotten logins

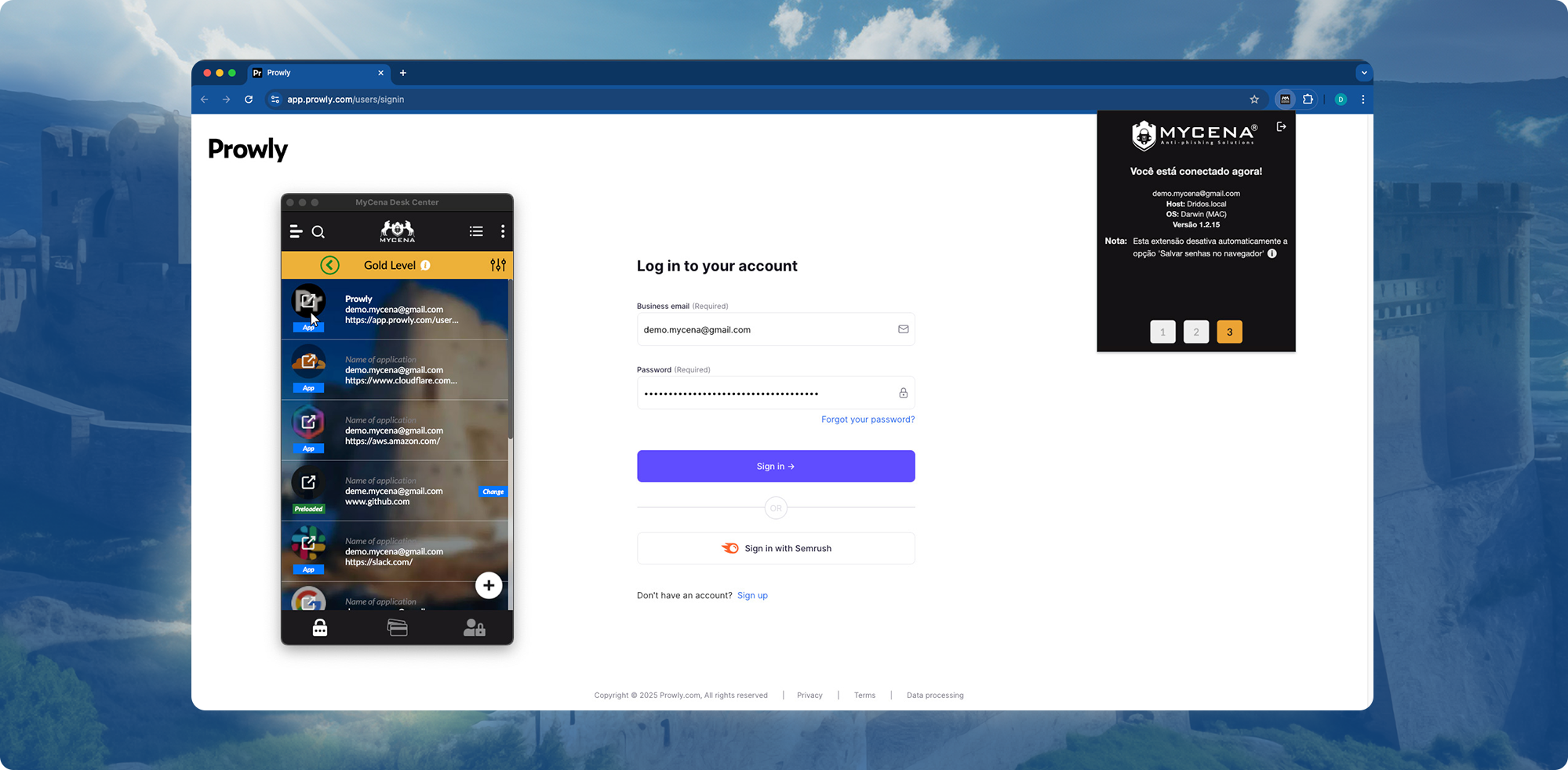
Click-and-go access to systems—no MFA fatigue, no shared secrets.
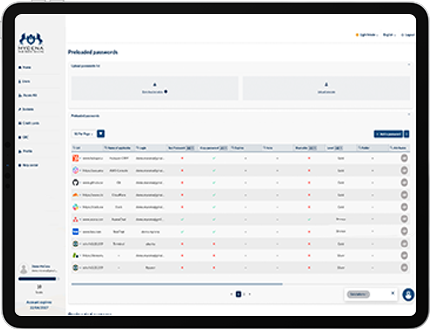
Generate GDPR and SOC2 audit trails instantly.

Attackers can’t jump systems—each credential is isolated.
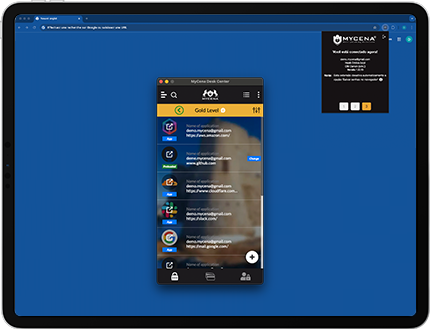
Vendors get limited, invisible credentials—access ends when they do
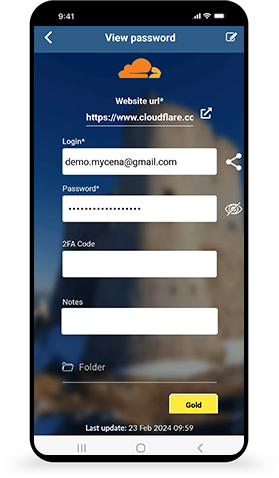

For Business Protection
Security
For Third-Party Risk Management
Resilience
Everything in Security, plus:
For Regulatory Compliance
Governance
Everything in Resilience, plus: