

Shared access and retained credentials open doors for fraud
Brute-force tools test billions of stolen credentials in minutes
Ex-employees and contractors retain system access for weeks
Push exhaustion and SIM-swaps bypass second-factor security
Vendors with overprivileged, unmonitored access enable lateral attacks
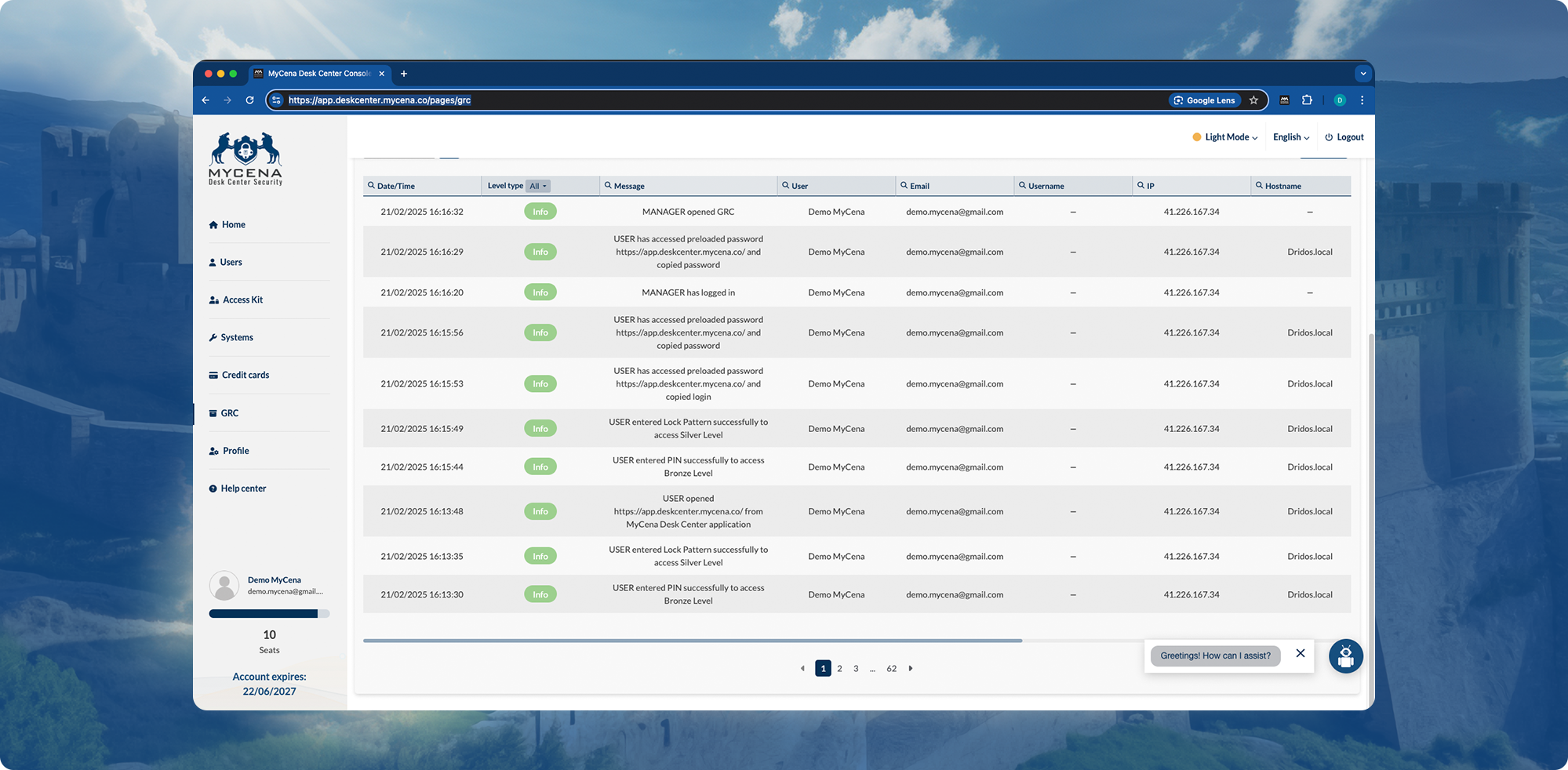
Weeks spent chasing logs across fragmented systems

– Julia O’Toole, MyCena® Co-CEO
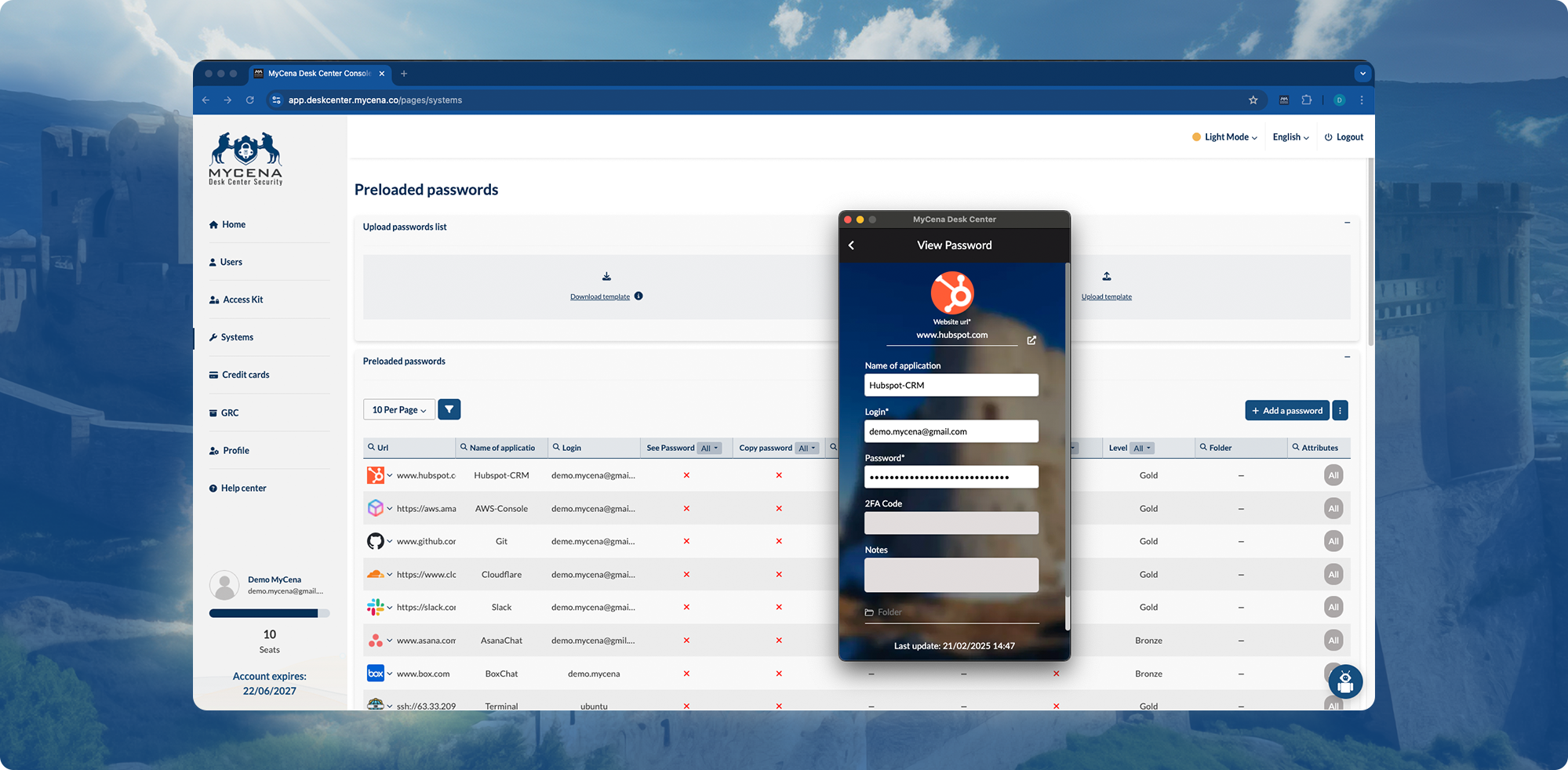
Users never see or manage credentials
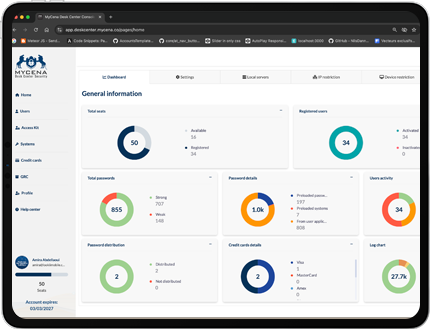
Eliminates helpdesk burdens and improves uptime

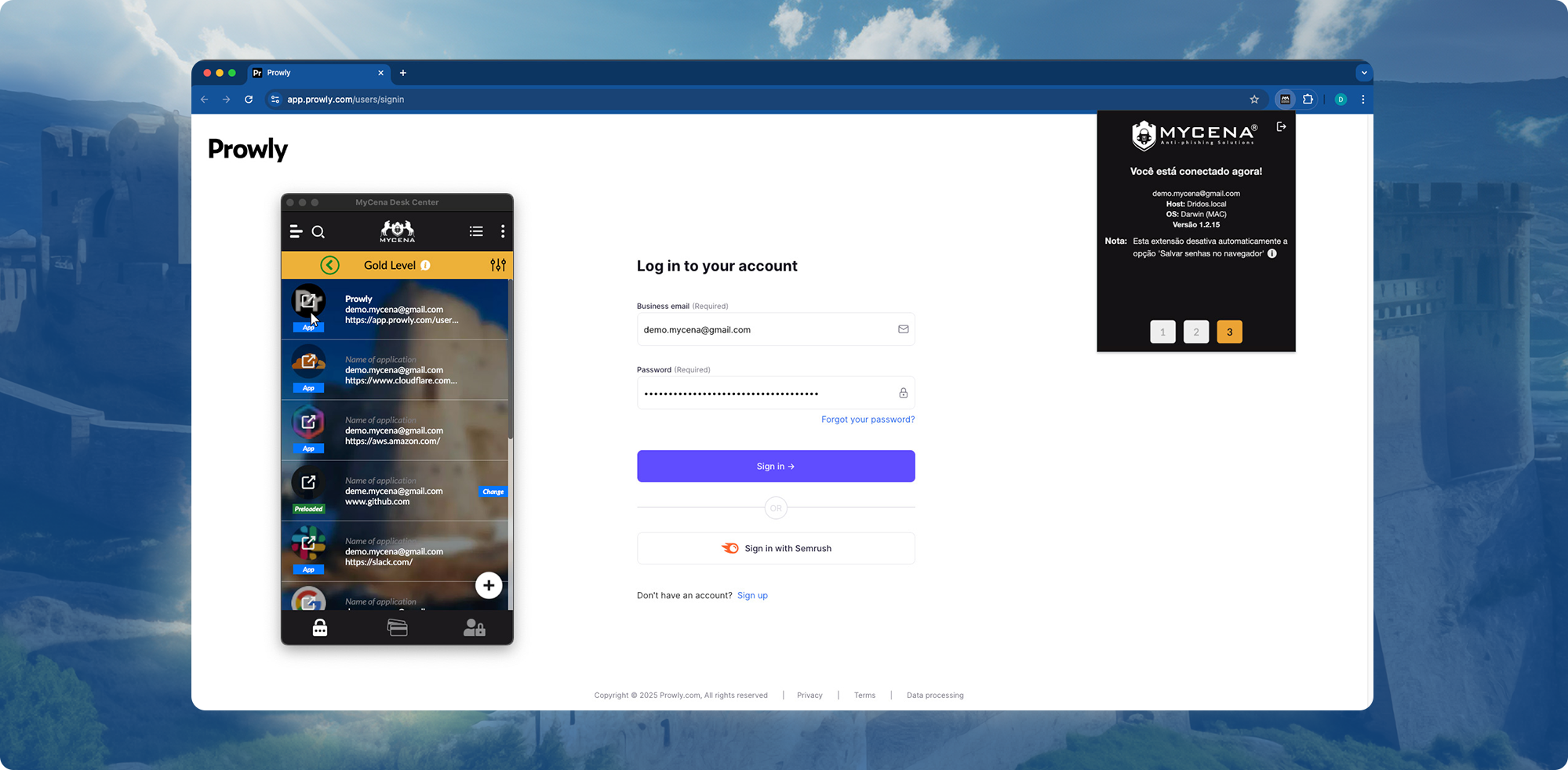
No shared secrets, no lateral movement
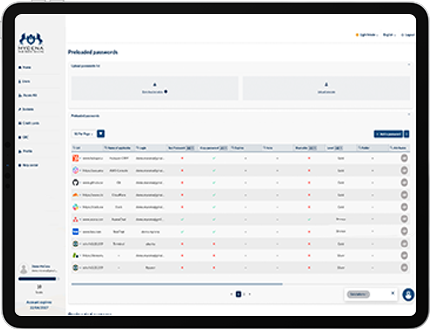
Immutable cryptographic access records — no screenshots or reconciliations

Auto-expiring, non-reusable access keys with scoped permissions
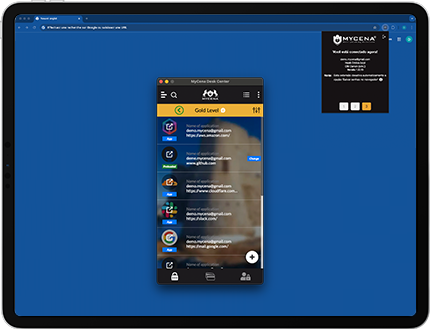
Grows across global teams without growing credential sprawl
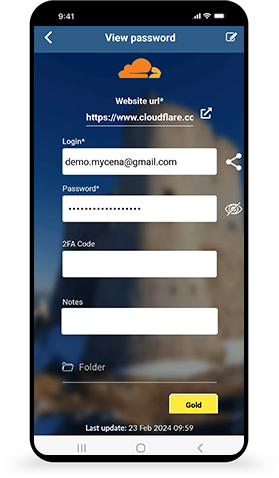

For Business Protection
Security
For Third-Party Risk Management
Resilience
Everything in Security, plus:
For Regulatory Compliance
Governance
Everything in Resilience, plus: