

86% of breaches involve stolen credentials, fueling ransomware and identity-based attacks.
AI-driven phishing bypasses MFA, tricking employees into credential exposure.
Attackers use stolen credentials to move undetected across networks.
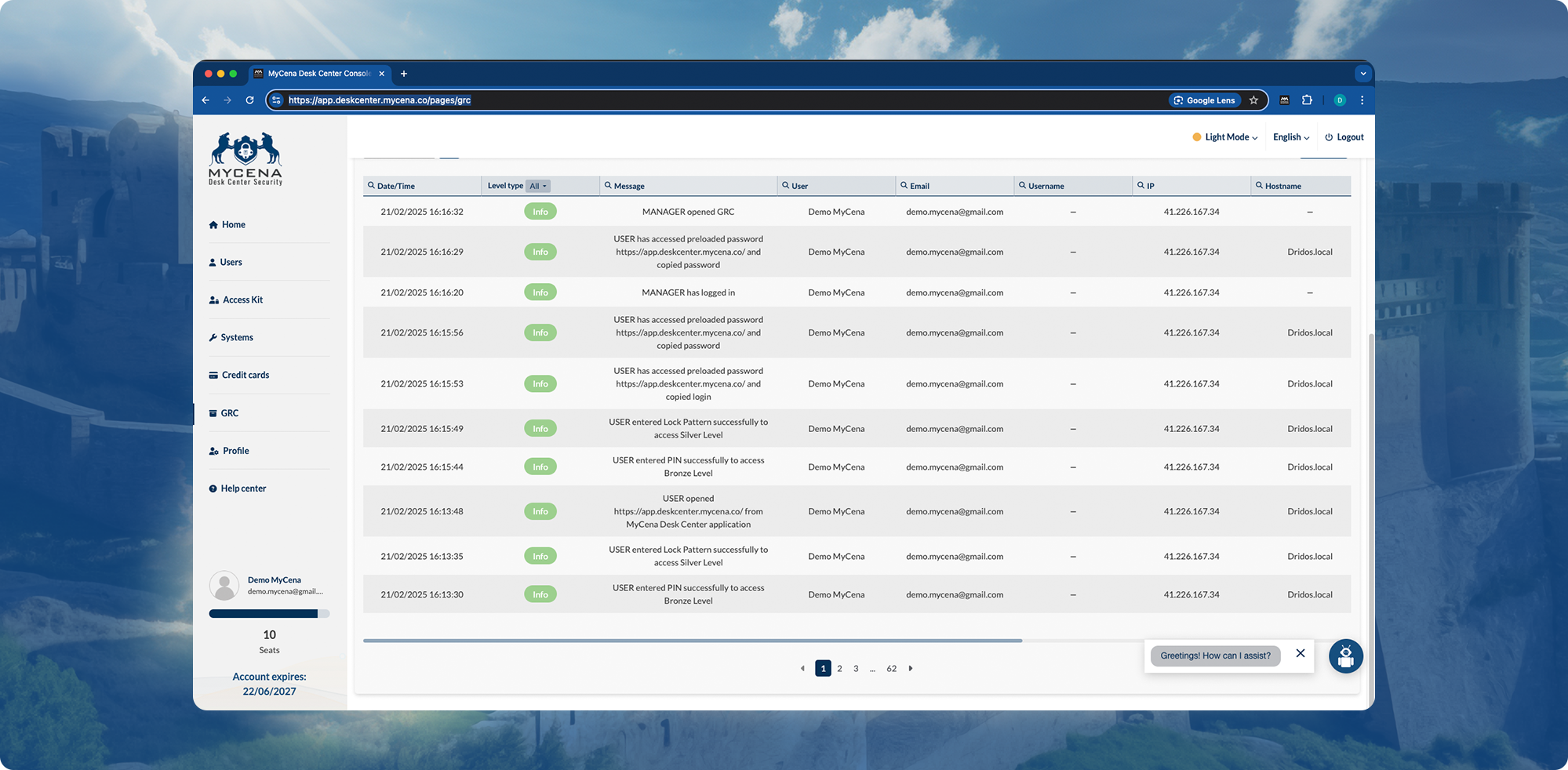
Weak authentication violates GDPR, DORA, NIS2, and ISO 27001 security mandates.
IT helpdesk burden—40% of tickets stem from password-related issues.
Third-party credentials expose enterprises to cascading security failures.



In the physical world, imagine if companies let their employees cut their own office keys, that would be mad. So why are we doing that in the digital world?
– Julia O’Toole, MyCena® CO-CEO
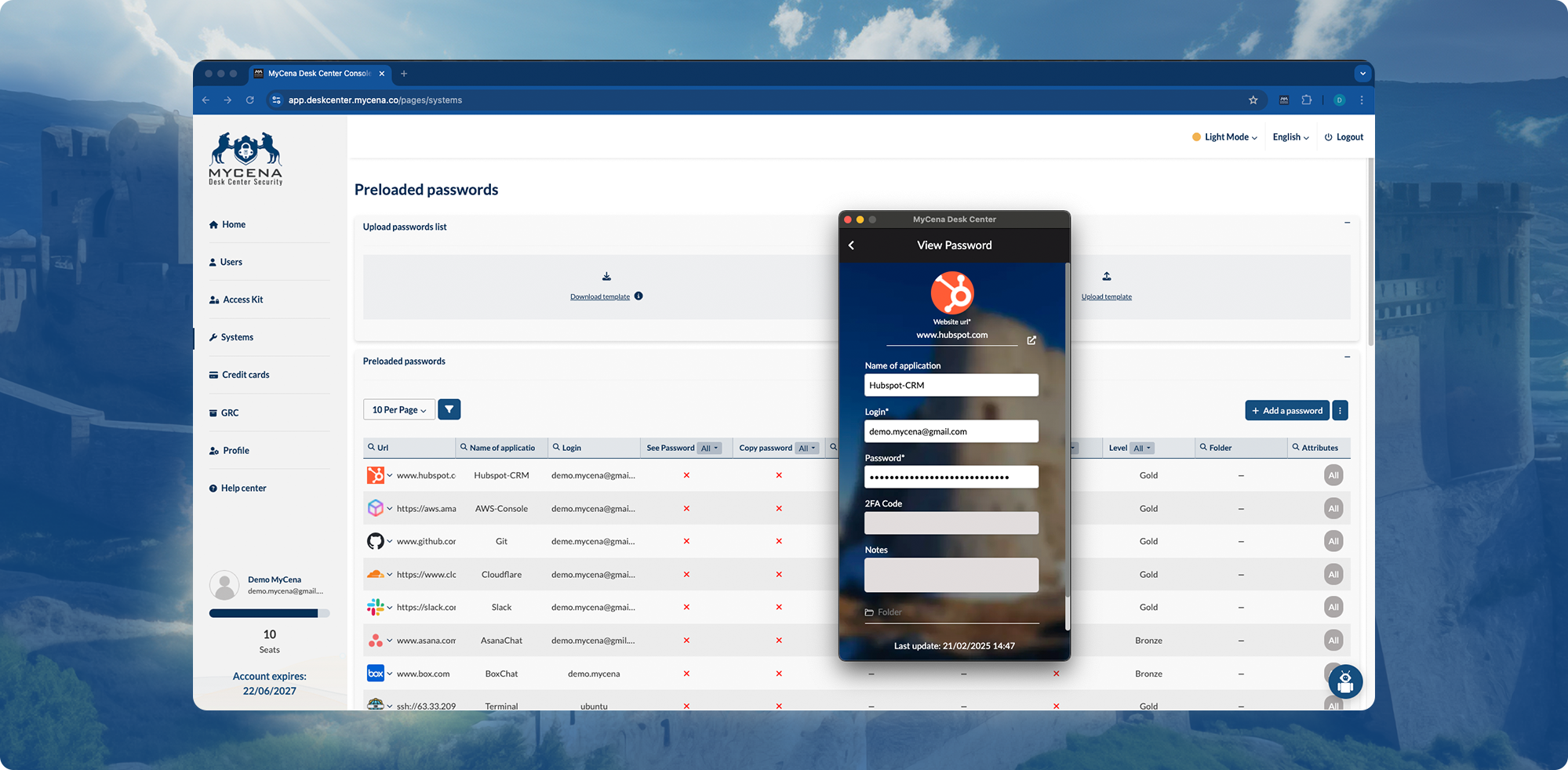
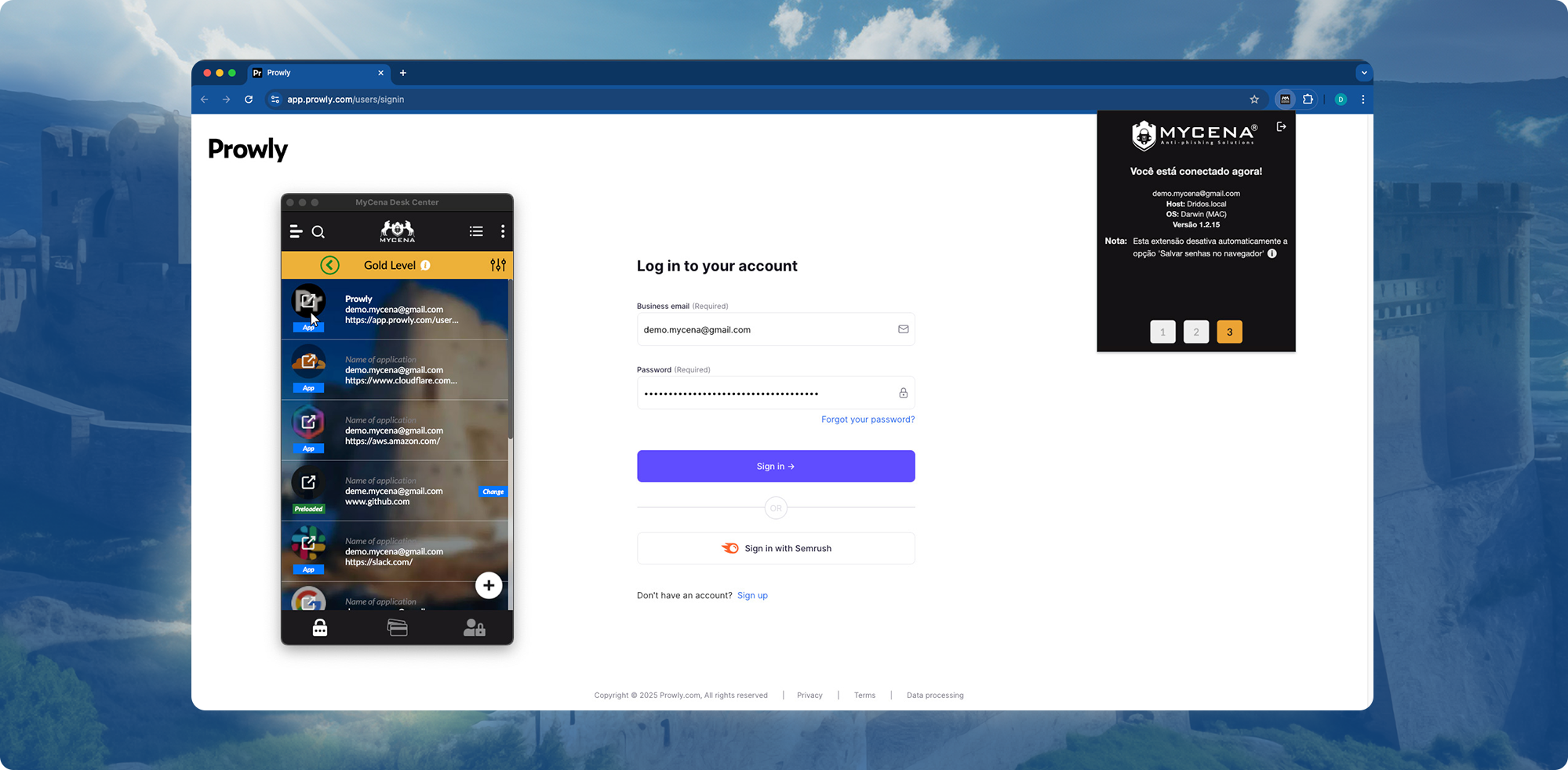
Eliminates human-managed credentials, preventing phishing attacks at the source.
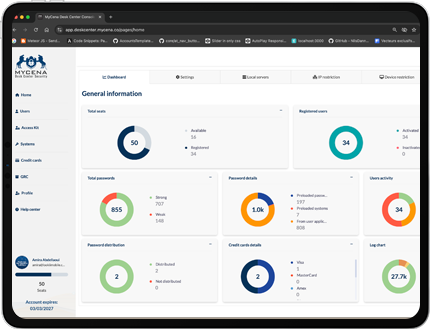
Stops IT helpdesk overload from forgotten or compromised passwords.

Users log in securely without managing credentials.
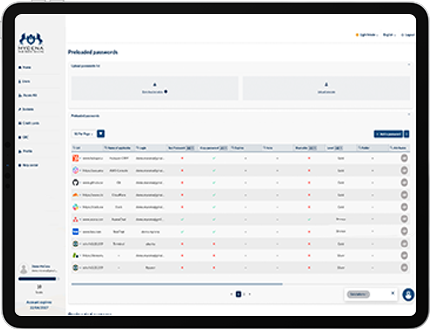
Meets GDPR, DORA, NIS2, and ISO 27001 effortlessly.

Encrypted, segmented credentials eliminate lateral movement risk.
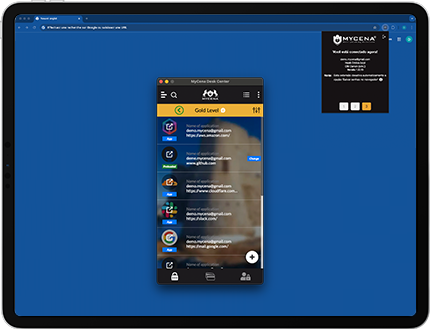
Prevents vendor credential leaks and supply chain attacks.
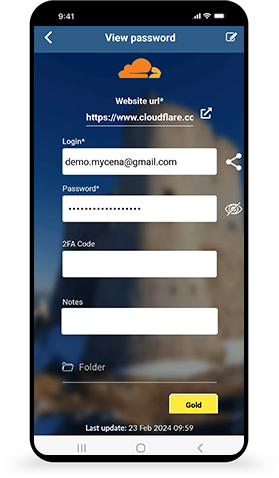

For Business Protection
Security
For Third-Party Risk Management
Resilience
Everything in Security, plus:
For Regulatory Compliance
Governance
Everything in Resilience, plus: