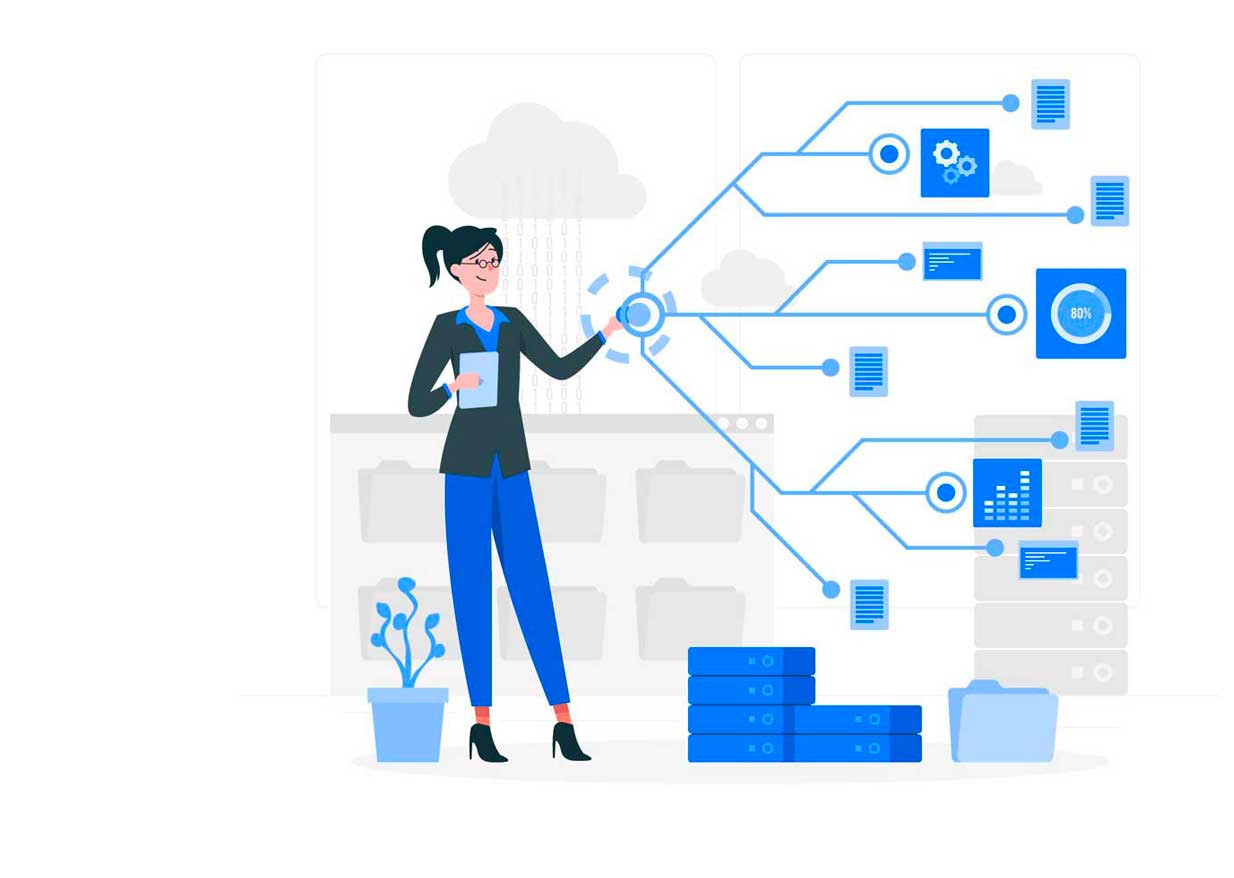

Traditional IAM, PAM, and SSO expose credentials, increasing phishing and ransomware threats.
98% of attacks target stolen credentials, causing massive financial and reputational damage.
40% of IT workload is wasted on password resets and access issues.
Proving regulatory compliance is complex, with gaps in access control logs.
Vendors and contractors introduce security gaps through weak credentials.
Insurance premiums rise due to credential-based risks, increasing operational costs.



In the physical world, imagine if companies let their employees cut their own office keys, that would be mad. So why are we doing that in the digital world?
– Julia O’Toole, MyCena® CO-CEO
Users never see or manage credentials, eliminating phishing risks
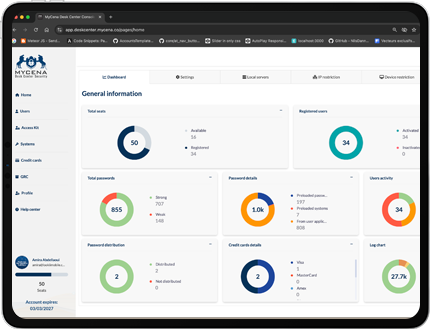
Reduces IT workload by 40%, freeing up resources.

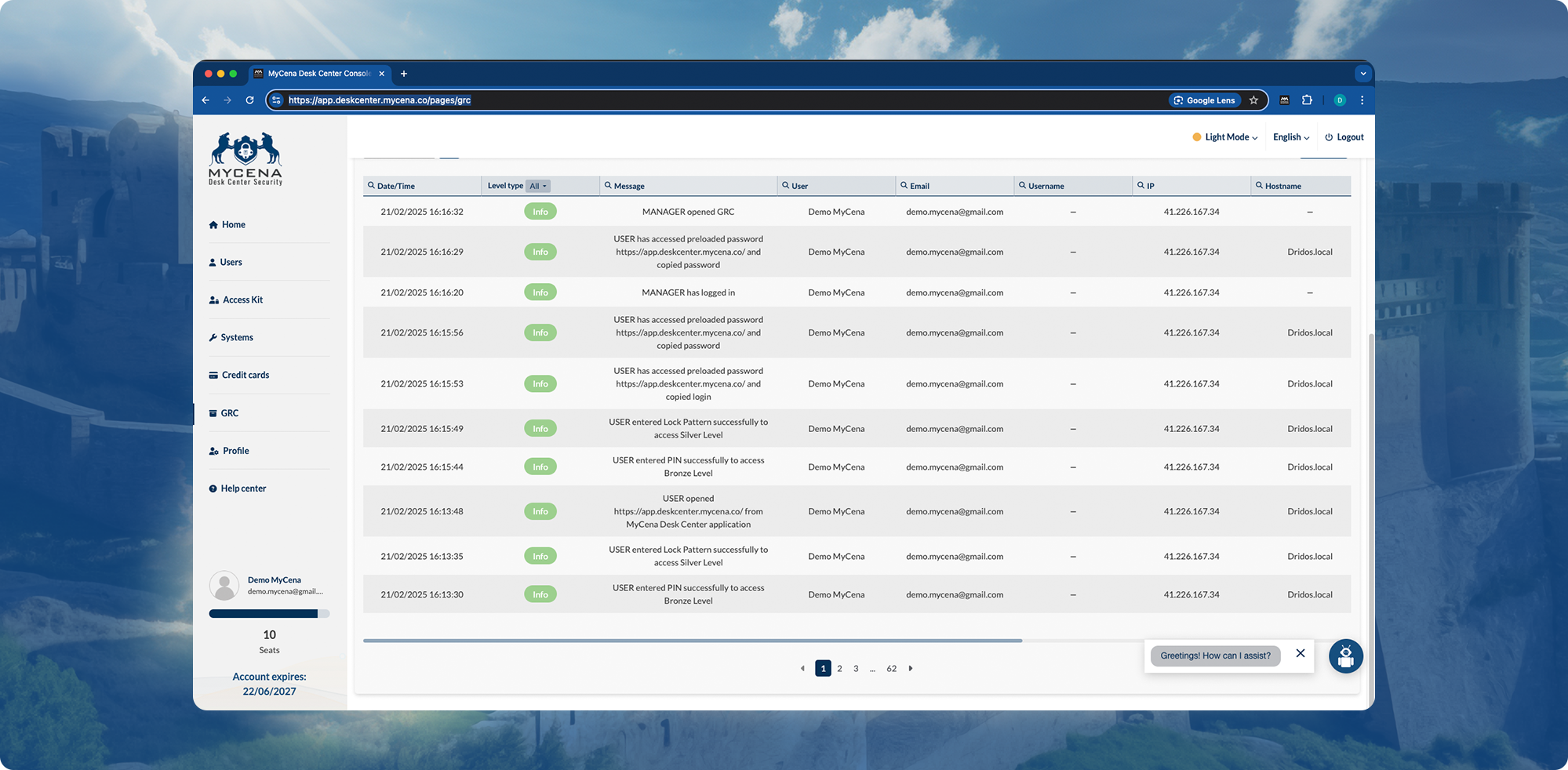
Automates access security audits for GDPR, NIS2, DORA, and ISO 27001.
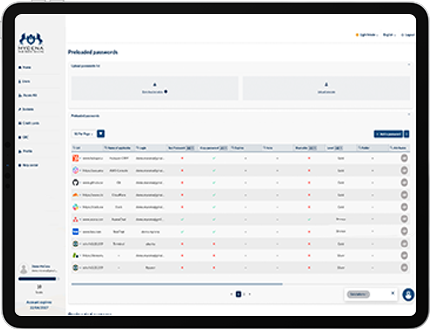
Centralized, automated credential distribution for employees and third parties.

Eliminates third-party credential leaks, ensuring zero trust security.
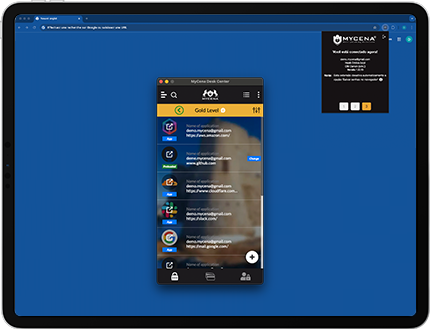
Eliminating credential risks leads to lower premiums and financial protection.

For Business Protection
Security
For Third-Party Risk Management
Resilience
Everything in Security, plus:
For Regulatory Compliance
Governance
Everything in Resilience, plus: